AI-Ready
SDLC Governance at Scale
Gain full SDLC context to ship trusted software faster.
Automate compliance and connect Dev, Sec, and Ops
to make every commit traceable and every release trusted.








Trusted by


With Chainloop enterprises benefit from centralized trusted storage, ensuring secure and verifiable data management.
A curated library of policies streamlines governance by providing standardized compliance frameworks.
An inventory of requirements helps track and enforce regulatory obligations efficiently.
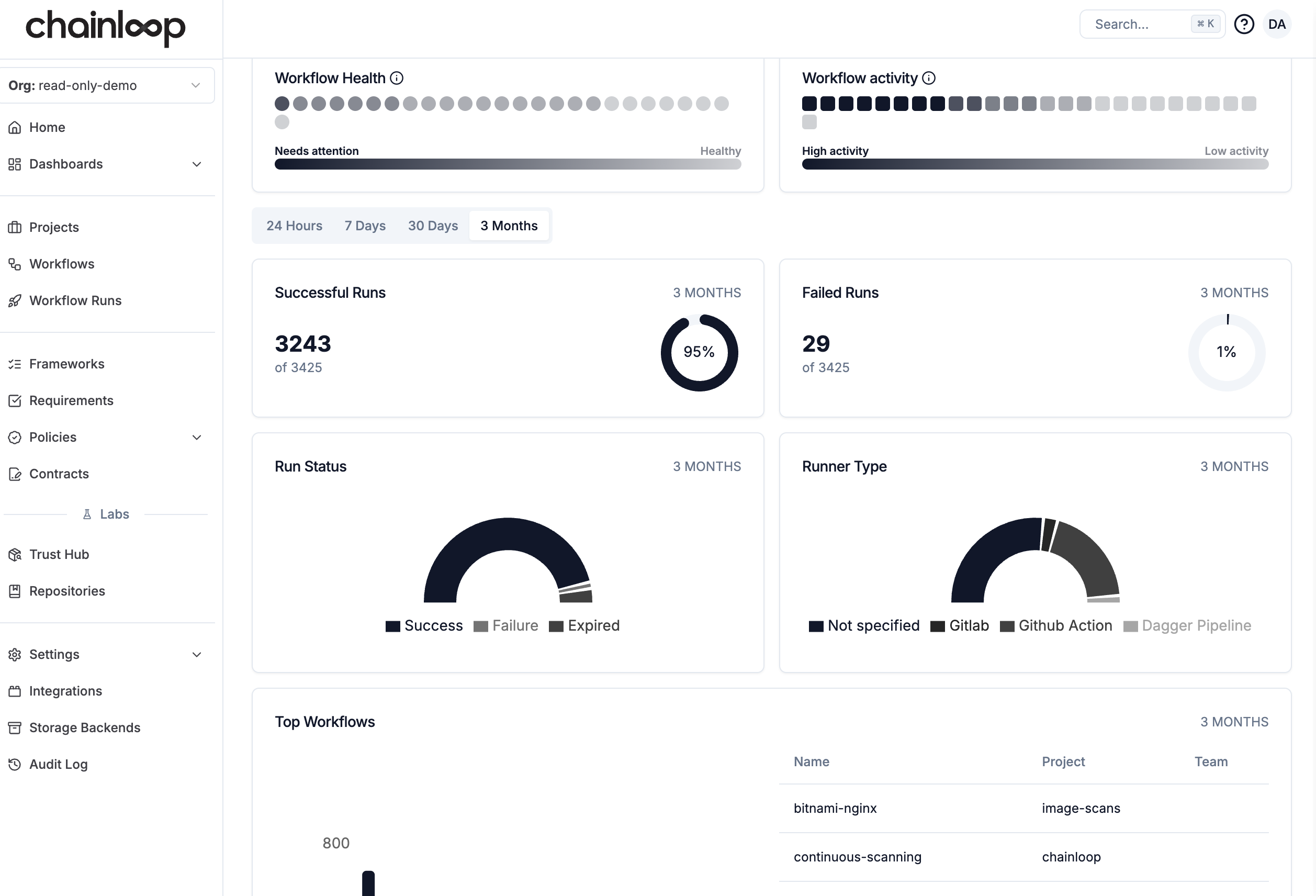
Unified dashboards offer a comprehensive view of compliance status, risk, and security posture in real time.
cross-team colaboration
Chainloop breaks down silos by connecting teams, fostering seamless collaboration and building trust across the entire organization. By unifying artifact management, compliance automation, and real‑time visibility into one centralized platform, Chainloop transforms complex, fragmented processes into a smooth, integrated workflow.
What They Do
Developers write code and push changes, triggering CI/CD pipelines that automatically capture build artifacts, compliance evidence, and security metadata. They also receive direct feedback—based on requirements, policies, contracts, and frameworks—right in their CI/CD job.
The Value & Biggest Painpoint
Instead of spending countless hours on Zoom calls or sifting through endless Google Docs to answer compliance questions, developers get automated, contextual security and compliance feedback that lets them focus on coding. Developers often spend time manually gathering and validating compliance data. Chainloop automates evidence collection and provides rich context with every commit.
Life With vs. Without Chainloop
With Chainloop, compliance feedback is integrated into the pipeline and issues are automatically flagged; without it, developers waste time in meetings and manual reviews.
How They Interact
DevOps engineers configure integrations, monitor unified dashboards, and leverage automated quality gates to ensure that every deployment meets regulatory and operational standards.
What They Do
DevOps teams integrate Chainloop into their CI/CD pipelines and workflows, ensuring that quality and control gates are automatically established for production deployments.
The Value & Biggest Painpoint
By consolidating multiple DevSecOps tools into a single platform, Chainloop accelerates delivery and removes repetitive, manual tasks, letting teams focus on high-value activities.DevOps teams often struggle with fragmented toolchains and manual compliance checks that delay deployments. Chainloop unifies data streams and automates quality gates, reducing bottlenecks.
Life With vs. Without Chainloop
With Chainloop, deployments are streamlined,centrally verified and guardrails are automatically enforced; without it, teams juggle multiple tools and spend excessive time on manual reconciliations.
How They Interact
DevOps engineers configure integrations, monitor unified dashboards, and leverage automated quality gates to ensure that every deployment meets regulatory and operational standards.
What They Do
Set security enforcements, create and apply policies, and ensure compliance across teams and pipelines. They monitor the overall security posture to detect and mitigate risks. Security and compliance professionals are responsible for setting and enforcing policies across various tools for SAST, DAST, IaC, vulnerability management, SBOM quality, and more.
The Value & Biggest Painpoint
Chainloop centralizes scattered compliance and security requirements into one platform, offering complete visibility and automating risk assessments. This eliminates the tedious manual audits and fragmented policy management that typically slow down teams.
Life With vs. Without Chainloop
With Chainloop, security and compliance are continuously monitored and automatically enforced; without it, teams struggle with disjointed systems and manual processes that delay risk identification and mitigation. Manual audits and inconsistent compliance checks can be time‑consuming and error‑prone. Chainloop automates risk assessments and continuously validates evidence, creating a tamper‑proof audit trail.
Manual audits and inconsistent compliance checks can be time‑consuming and error‑prone. Chainloop automates risk assessments and continuously validates evidence, creating a tamper‑proof audit trail.
How They Interact
They use intuitive dashboards and policy configuration tools to setup frameworks, requirements and policies, monitor CI/CD pipeline risks, review risk assessments, and manage compliance exceptions, ensuring a robust security posture.
What They Do
Executives, team leads, and managers oversee cross‑team collaboration, monitor compliance, and track the health of the CI/CD pipeline through consolidated dashboards. They ensure alignment with business objectives and strategic priorities.
The Value & Biggest Painpoint
Chainloop provides a unified view of the entire software supply chain, reducing the need to manage multiple tools and fragmented reports. This real‑time visibility empowers leaders to make data‑driven decisions, optimize costs, and ensure alignment with business objectives.
Without centralized visibility, executives struggle with fragmented data that hinders timely decision-making. Chainloop provides a single source of truth, giving leaders full insight into the SDLC and enabling them to approve exceptions quickly.
Life With vs. Without Chainloop
With Chainloop, executives enjoy comprehensive, real‑time insights into compliance and risk; without it, they rely on disjointed data and inefficient manual processes that hinder strategic decision-making.
How They Interact
Leaders access high‑level dashboards and executive reports that showcase aggregated SDLC metrics, risk prioritization, and compliance status, enabling streamlined approvals, exception management, and strategic oversight.
Chainloop centralizes all your software artifacts and compliance evidence into one secure system, automatically capturing key metadata from your CI/CD pipelines. Every piece of data is digitally signed and connected in a traceable, immutable graph, ensuring full visibility and a robust audit trail. With seamless integrations, automated policy enforcement, and continuous monitoring, Chainloop makes compliance effortless and provides real-time insights to help you build and deliver trusted software faster.
KEY FEATURES
Chainloop captures every artifact, CI/CD metadata, and compliance evidence, securely storing them with rich contextual information.
Graph-Based Provenance: every item is interconnected in a traceable graph, providing complete visibility over your software lifecycle.
Immutable Storage: digital signatures protect your artifacts by storing them immutably, ensuring a robust and verifiable audit trail.
Content Addressable Storage: Efficiently retrieve and manage stored artifacts, guaranteeing consistency and reliability.

How it works
Chainloop integrates directly into your CI/CD process to automate security and compliance checks —without slowing you down.
Metadata Generation
Developers produce key data—such as build artifacts, SBOMs, vulnerability reports, and other compliance evidence—during the software build process.
Easy Integration
DevOps integrate Chainloop into existing CI/CD pipelines using our CLI or integrations, automatically capturing all the necessary evidence with context (e.g., Git commit details and pipeline configuration).
Digital Signing
Every piece of metadata is digitally signed (using SLSA, in-toto, sigstore, or your own PKI such as AWS KMS or Keyfactor) to ensure it is tamper-proof and verifiable.
Centralized Storage and Validation
Signed data is pushed to our secure evidence store, where it is validated and organized into a comprehensive record.
Automated Policy Enforcement
Security and compliance teams define rules using our curated policy library. These policies are automatically applied, delivering immediate risk assessments and remediation guidance.
Continuous Monitoring
Our system continuously checks that every project meets your defined security and compliance standards.
Real-Time Insights
An intuitive dashboard provides instant alerts and clear reports to keep your teams informed.
WHAT OUR CUSTOMER SAY
Chainloop delivers compliance without friction transforming our complex security processes into a seamless, automated workflow.
Chainloop is a powerful CI/CD pipeline compliance tool for our DevSecOps and security policies. It offers comprehensive monitoring for all pipeline security requirements.
Fortune 500, USA
Chainloop is the missing piece that enables a sensible approach to SBOM management, as well as attestation and artifact management for our security teams.
CTO, System Integrator, USA
Audits that once took weeks or months are now completed in just hours—thanks to Chainloop.
Senior Executive Vice President, Platform Engineering, Large Bank, Asia
Chainloop empowers us to trace every commit and trust every release.
System Integrator, Gov Space, USA
Without Chainloop, meeting security requirements could take weeks or even months. It has significantly expedited our process.
Enterprise, USA
We rely on Chainloop as an enterprise-grade solution to automate compliance of the product and CI/CD pipeline security requirements... across hundreds of products.
Security & Compliance Team, Fortune 500, USA