Chainloop Changelog, January 2025
Miguel Martinez
TL;DR: This year, we’re making Chainloop the go-to platform for Sofware Supply Chain automated compliance and security. Expect a smoother developer experience, plug-and-play frameworks for frictionless CRA, SSDF, and SLSA compliance, advanced exception handling, and more---so you can focus on building
Policies evaluation CLI exposure
Developers can use the Chainloop CLI to instrument their CI/CD systems, send required evidence, and comply with security and compliance policies.
Now, in addition to the information shown to security and compliance operators in the UI, the CLI also shows policy evaluations during the attestation process to reduce the turnaround time for compliance remediation.
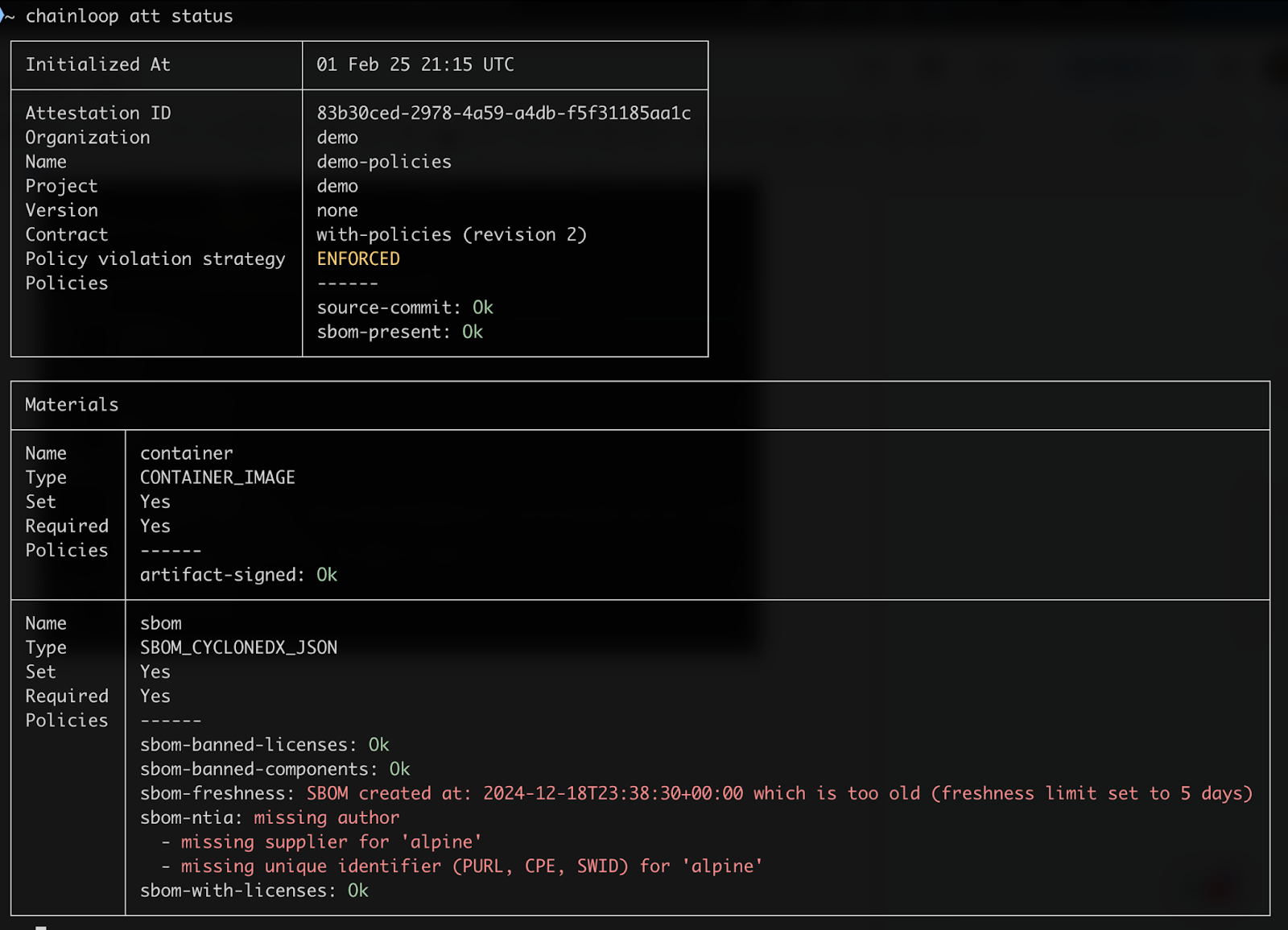
In this example, Chainloop, after being instructed by the compliance team to run SBOM quality and artifact integrity policies, tells the developer that their SBOM is too old and doesn’t meet the NTIA minimum requirements. On the bright side, they got the go-ahead to ensure the commits and container images are signed.
Enforced by Default Policy Violation Strategy
Security and Compliance teams can set policy evaluation strategy to ENFORCED by default in their organizations.
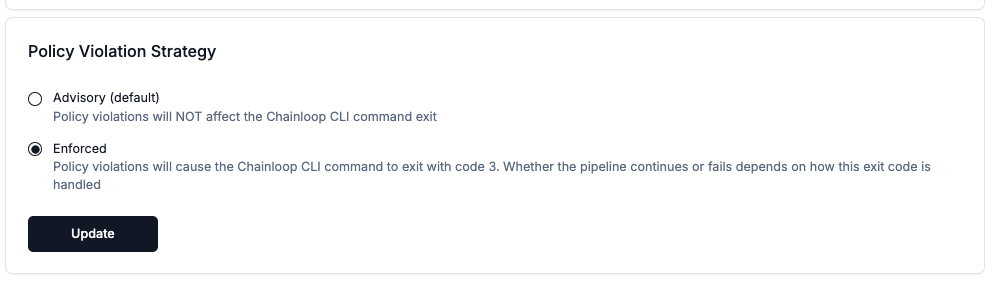
This means that during any attestation process that contains policy violations, the CLI will return with an error code in addition to recording the attestation result and the fact that the pipeline was blocked.
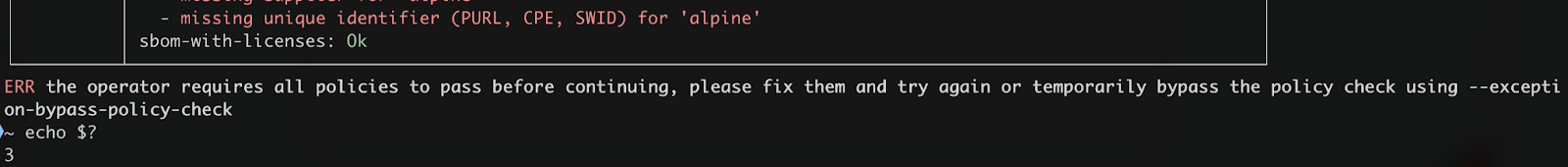
But I can hear what you are saying. Breaking pipelines might not be a good idea! We hear you. That’s why developers can provide the flag “—exception-bypass-policy-check” as an exception path when unblocking their pipelines.
This will make their CI pipeline run as expected, but the exception has been recorded and exposed to the compliance team for verification.
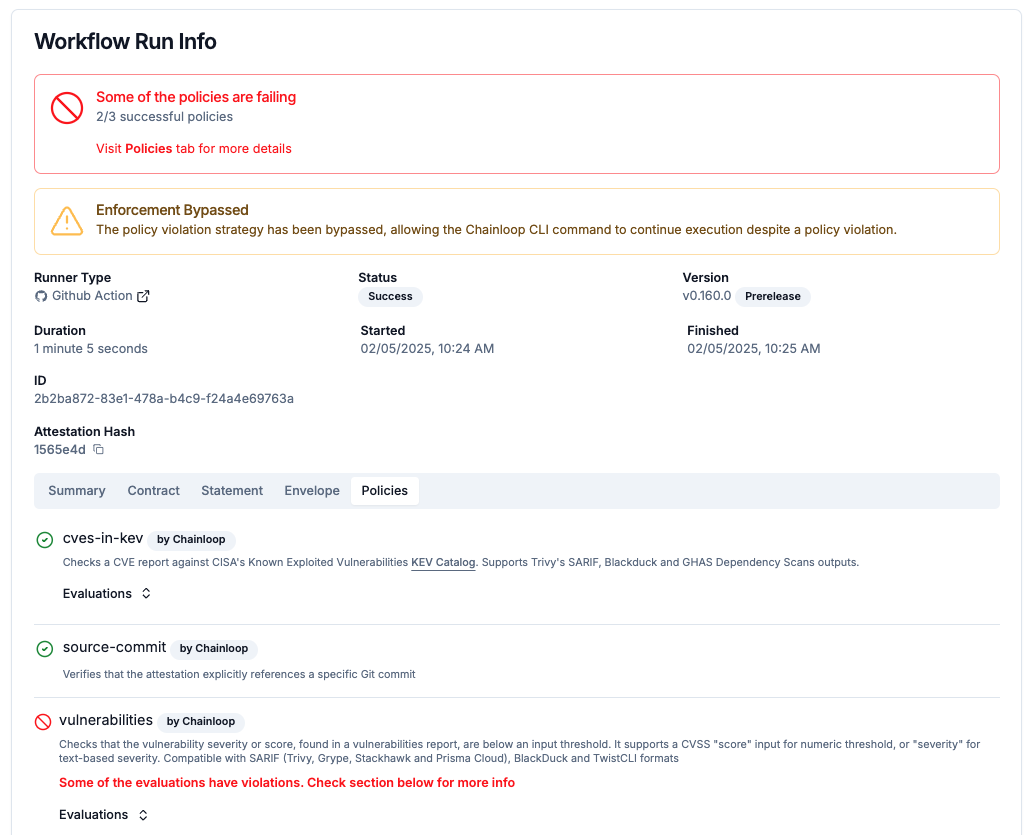
Best Practices Compliance Framework
In addition to allowing our users to define their custom compliance frameworks, we are starting to expose a curated set of frameworks and requirements that can be used out of the box.
Today, we are releasing the “Chainloop Best Practices” framework preconfigured with some popular SCA, SAST, and integrity requirements.
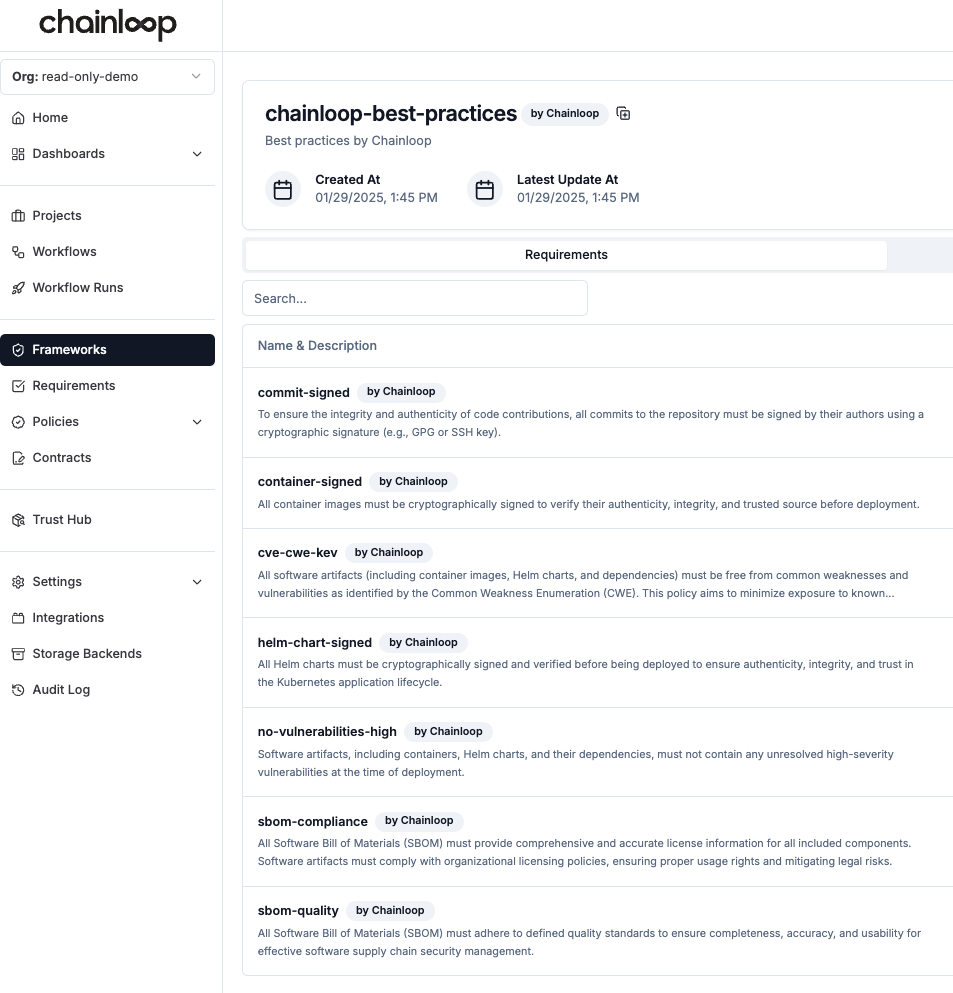
This is just the first step. In the future, you should expect more frameworks, including external compliance frameworks like the Cyber Resilience Act (CRA), Secure Software Development Framework (SSDF), and more.
Requirements exception support
When you attach a compliance framework to a project, a set of expected
requirements will be tracked over time, filling up your compliance and
security posture.
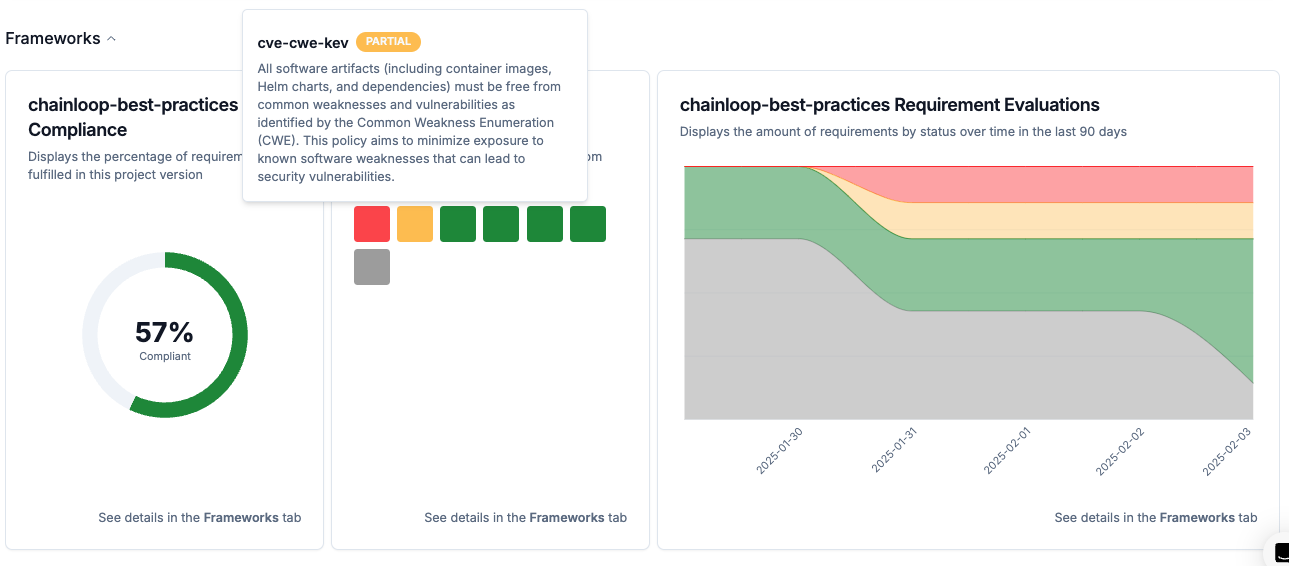
In some scenarios, not all requirements can be met before performing a release, so an exception mechanism must be implemented.
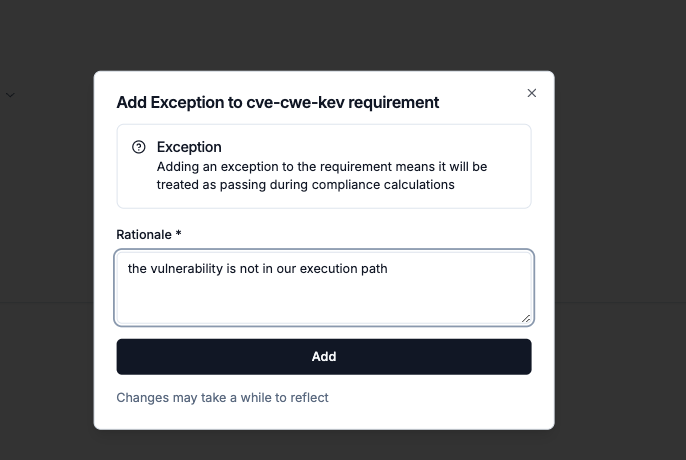
You can now add exceptions to any requirement.
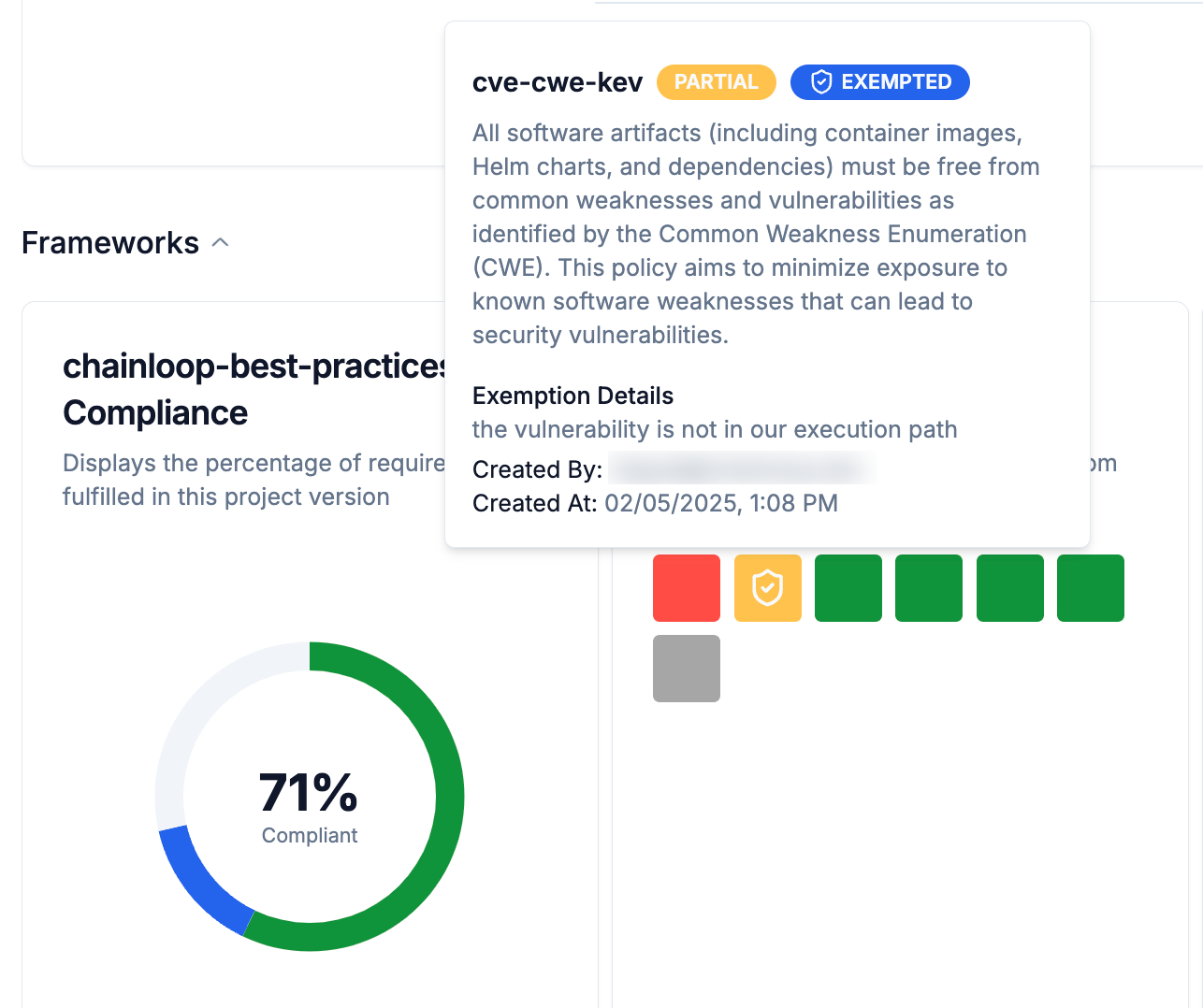
The exception will now be considered when calculating the compliance and security posture and recorded in the audit log.
Wrapping up
We are gearing up for the general availability of our platform, but until then, we’ll be happy to give you private access and show you a demo. Let’s chat!


