Chainloop Changelog, July 2024
Miguel Martinez
It’s summertime on this side of the hemisphere, but that hasn’t stopped our team from adding more capabilities to the Chainloop Platform.
Chainloop Evidence Store
Let’s start with some highlights for the Chainloop Evidence Store open-source project.
Attestation Policies
Today, we are happy to introduce a feature that extends and enhances our concept of Workflow Contracts. Policies. Policies are a foundational component for use-cases like Software Bill of Materials (SBOM) quality gates, vulnerability management, OSS license compliance, just to mention a few.
Operators can now attach Rego policies to their workflows. During the attestation process, these policies will be automatically evaluated against any matching pieces of evidence (e.g., SBOM, SARIF, …) or attestation metadata (in-toto statement).
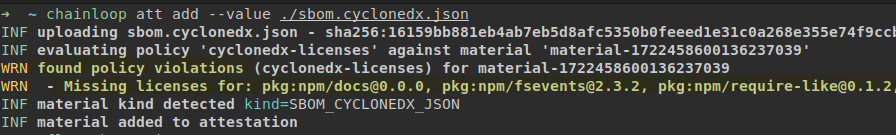
The evaluation result is included as a list of violations and added to the attestation statement before it is signed and sent to Chainloop.
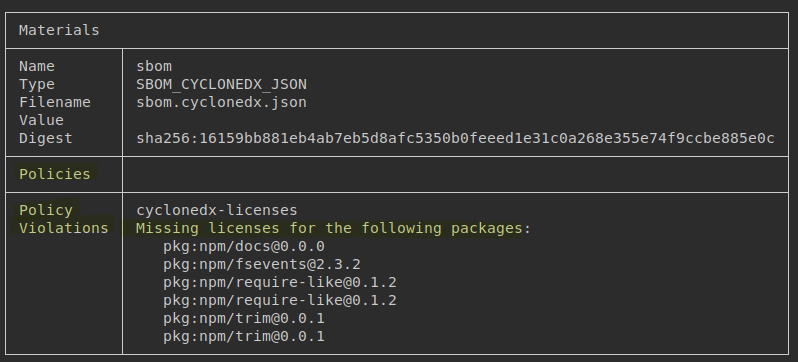
This is just the beginning. We are excited to see what kind of policies the community will build with this framework. To learn more, refer to our documentation.
Monitor your CI/CD with Chainloop and Prometheus
Have you ever had CI jobs that have been failing and not noticed? Are you tired of how each CI/CD provider has (or lacks thereof) its own way of providing visibility? Are you struggling with standardizing minimum CI/CD operational visibility practices across all your teams? Do you wish you could automatically bring this all to your familiar environment?
If you answered yes to any of those points, you will like what’s next. Today, we are happy to announce centralized CI/CD operational metrics through Chainloop as Prometheus metrics!
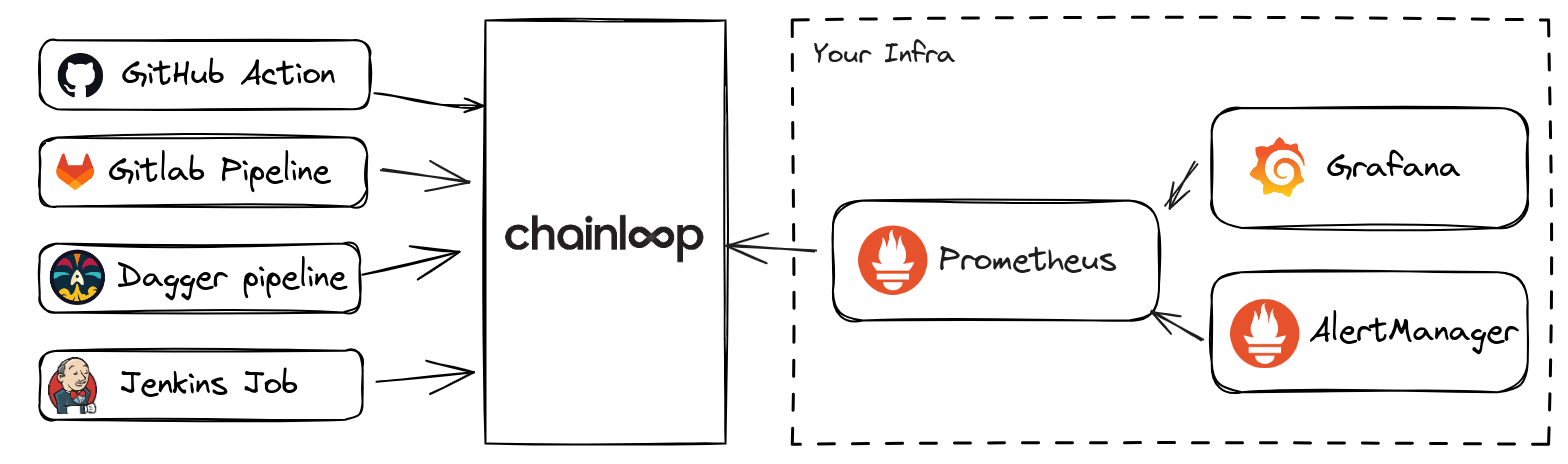
It doesn’t matter what or how many CI/CD systems you use. Now, Chainloop will gather information during the attestation processes and expose it through your authenticated Prometheus endpoint. All of that without the development team’s involvement! :)
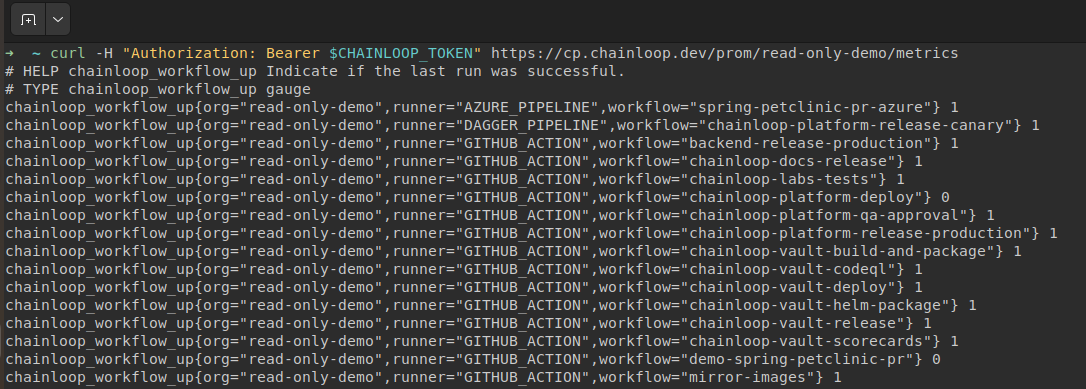
From here, the sky is the limit. You can craft and bring these metrics to your favorite Grafana dashboards and/or detect anomalies (and failed jobs) using AlertManager.
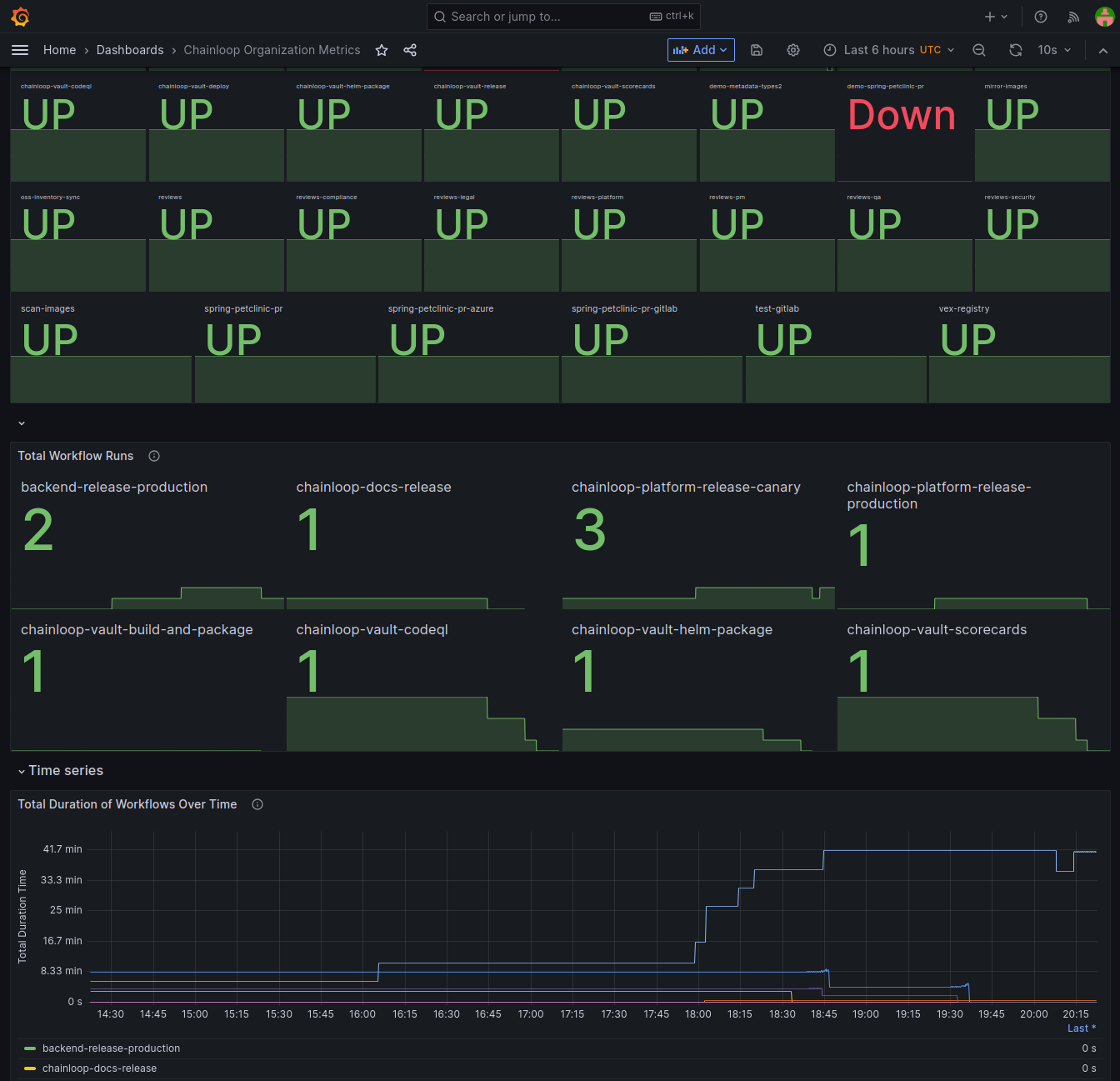
Read the docs to learn more about this feature and how to set it up.
Support for multi-stage attestation processes
By default, Chainloop requires the whole attestation process to happen end to end in the same environment. This requirement made it very difficult to implement attestation processes in parallelized or distributed CI pipelines.
For example, the pipeline below runs parallel CVE scans and container image relocations. Scan results are gathered in different jobs, and the attestation is signed and pushed at the end.\
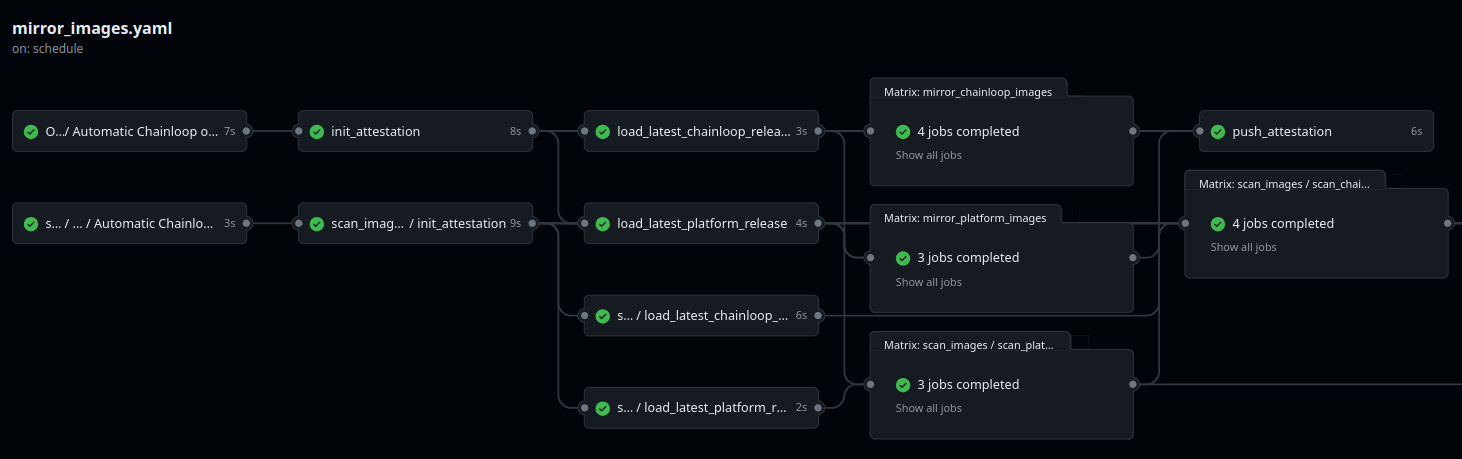
To support this scenario (and also stateless clients like our Dagger
module),
we implemented a feature called “attestation remote state”. Simply
put, instead of the attestation CLI being in charge of maintaining the
state during the attestation, this can be delegated to the server and
retrieved at any time by providing the "attestation-id”.
Note that this feature is optional, to enable it, you must provide the flag “—remote-state” to the “attestation init” command.
Chainloop Platform
Next, let’s discuss features added to the Chainloop Platform. The Chainloop platform is a product built on top of the OSS Chainloop evidence store. It’s currently in private early access and available in two versions: SaaS and on-prem.
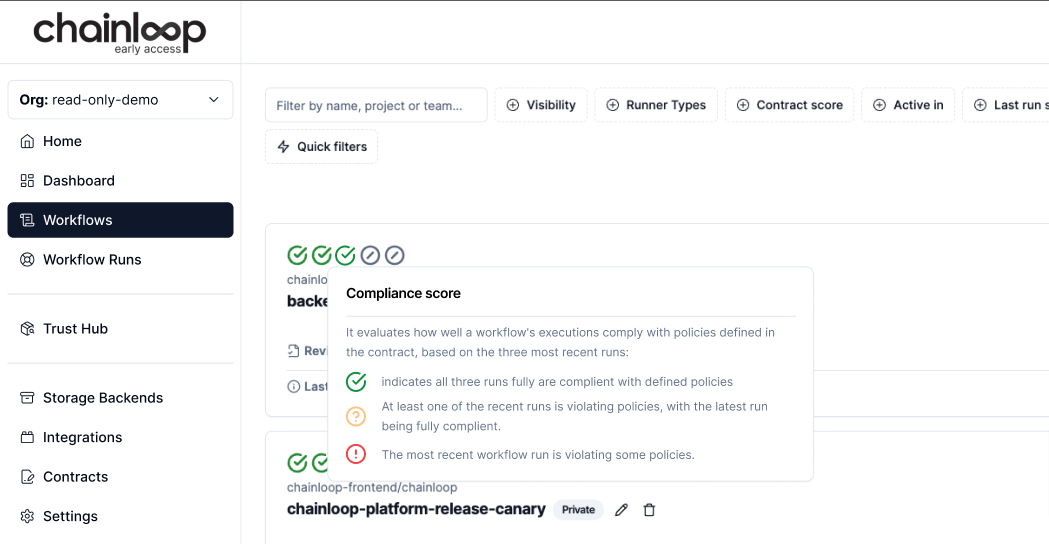
Policies Preview
You can now get real time policy evaluation information in the UI, either as part of the comprehensive compliance score.
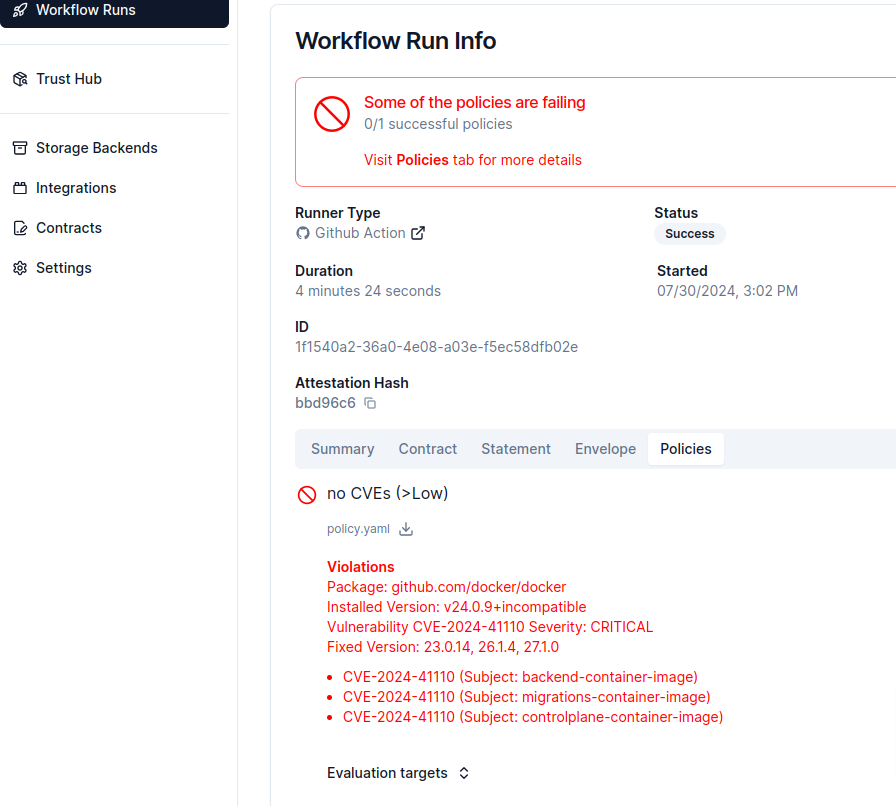
Or digging deeper into the policy results.
White-labeling support
Our design partners have been asking about offering custom experiences in their organizations. Chainloop platform UI has the foundations to provide white labeling, starting with a configurable page. More to come :)

On-prem relocation, Airgap, and FIPS support
Deploying Chainloop platform in Kubernetes just got much better. It’s now compatible with relocation processes performed by the Helm Relocation Plugin. This means you can easily take our packaged Helm Chart, and its associated container images and push it to your internal registry with just a couple of commands.
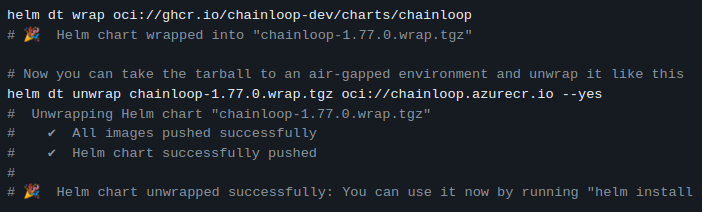
Lastly, we now offer FIPS-capable binaries and container images, let us know if you are interested!
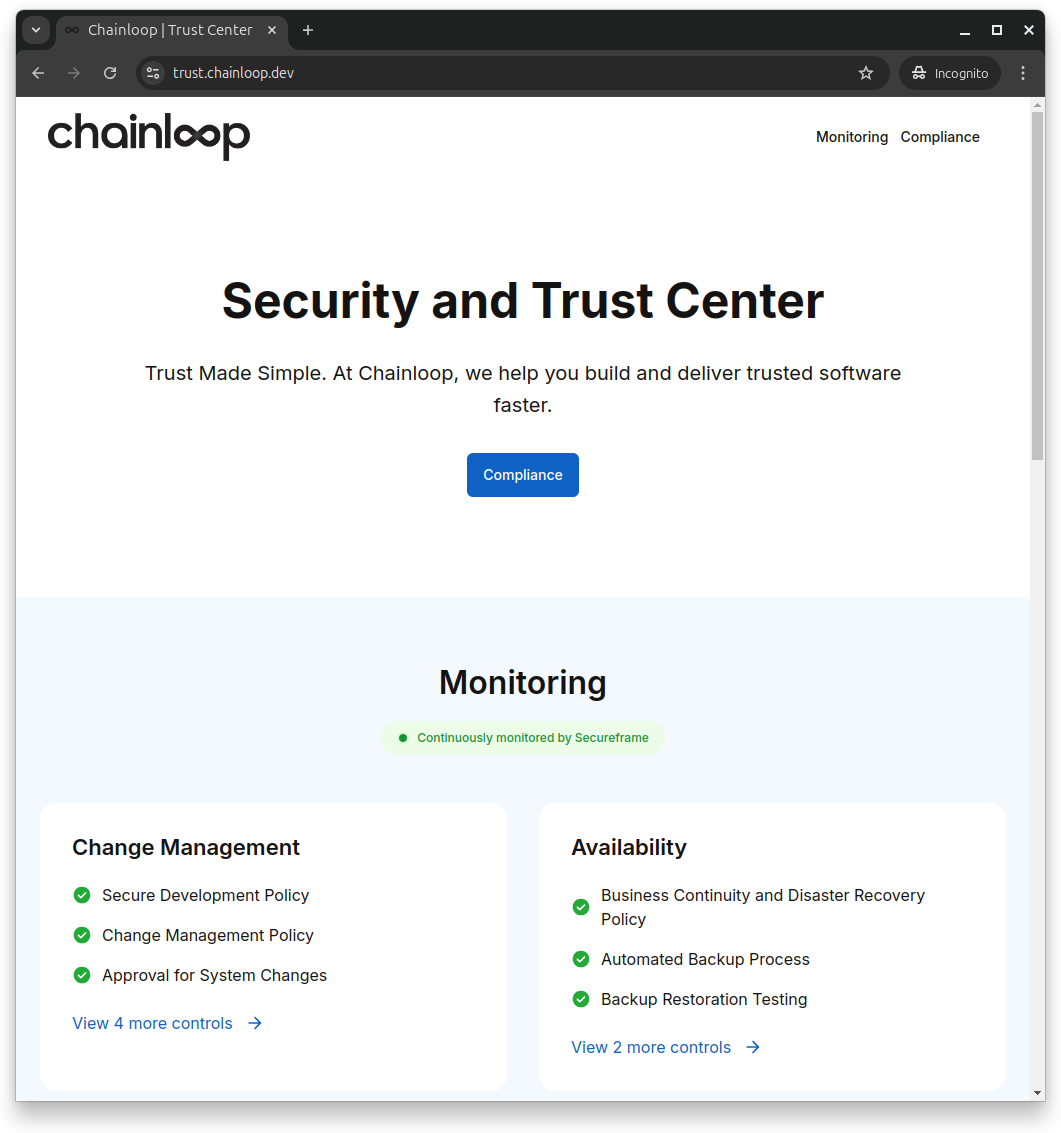
In-progress SOC-2 Compliance
Having a trust relationship with our customers and partners is at the core of our values. That’s why we’ve started the process of SOC-2 and ISO 27001 compliance.
You can now visit trust.chainloop.dev to follow its progress.
Weekly digests
You can now receive weekly snapshots of your organization’s operational and security posture via email.
This email includes information on what are the workflows that drifted out of compliance, as well as operational, and segmented metrics.
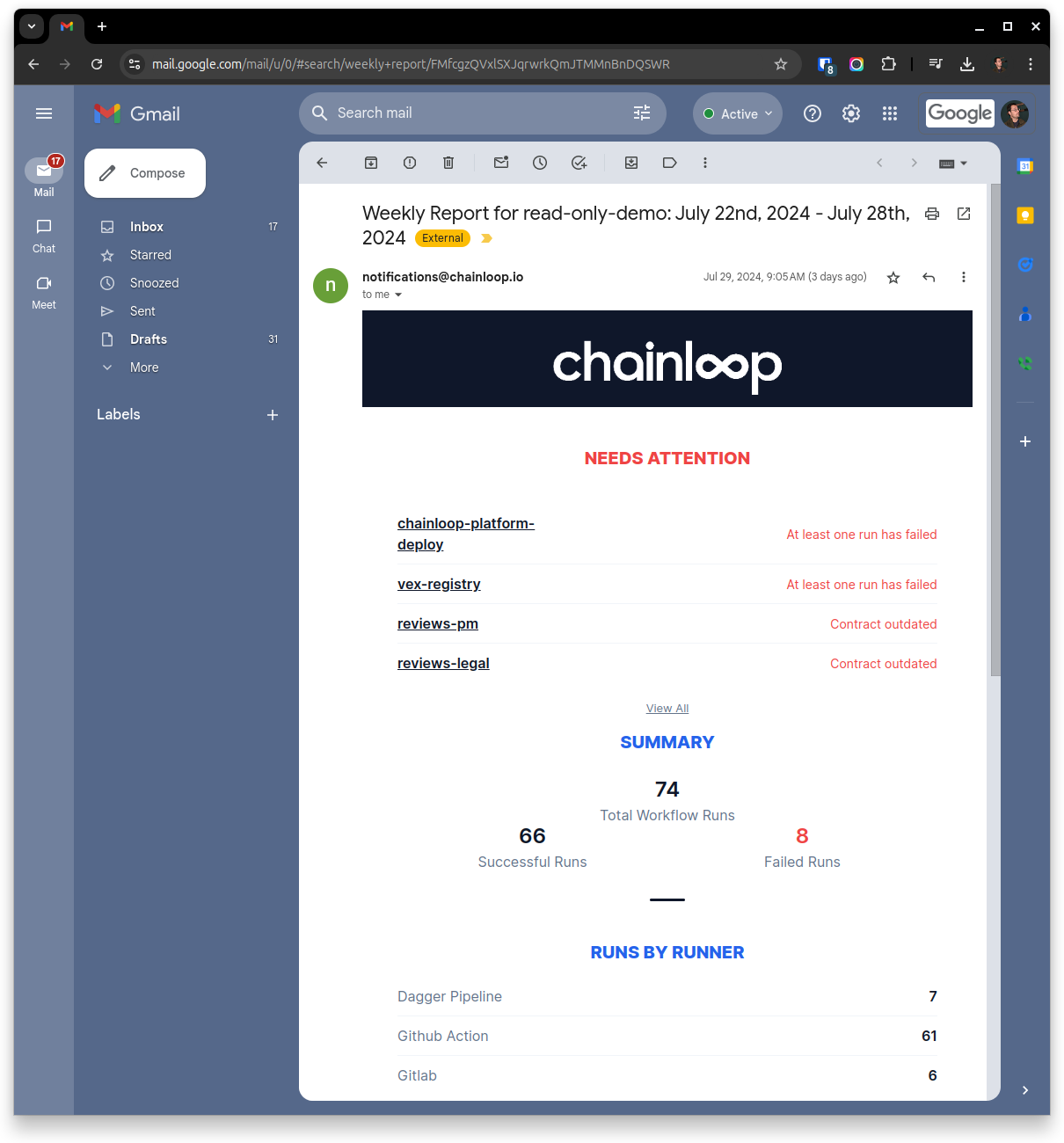
You should expect more notification mechanisms later on but for now, you’ll have a quick, actionable summary right in your inbox.
Wrapping up
That’s it for this month. Do you want to know more? Book a demo. We’ll be super happy to show you what we’re cooking.
If you like what we do, feel free to drop a contribution, join our community in Slack, or give Chainloop Open Source a star on GitHub chainloop-dev/chainloop :)


