Chainloop Changelog, September 2024
Javier Rodriguez
TL;DR: Summer has come and passed, we’ve coded and moved, another month, another packed one.
We have introduced key updates to the open-source evidence store platform, including integration with Keyfactor’s SignServer and EJBCA for remote and local signing. A new evidence type, GitLab security reports, is supported, and the Dagger module has been extended for workflow automation. Chainloop now retrieves Cosign and Notary signature info during container image attestations. Additionally, multi-kind policies have been added, enabling unified policy enforcement for different evidence formats like SBOMs.
On the platform side, new policies for secrets detection, SARIF vulnerability analysis, and CWE Top 25 detection have been introduced. There’s a focus on improving SBOM quality standards, and Chainloop CLI now supports Windows.
The company also achieved SOC 2 Type II compliance and continued partnerships, notably with Keyfactor, while engaging in industry events across Europe.
Chainloop Open Source - Evidence Store
Let’s start with the work done in our open-source project, Chainloop Evidence Store.
Integration with Sign-server and EJBCA
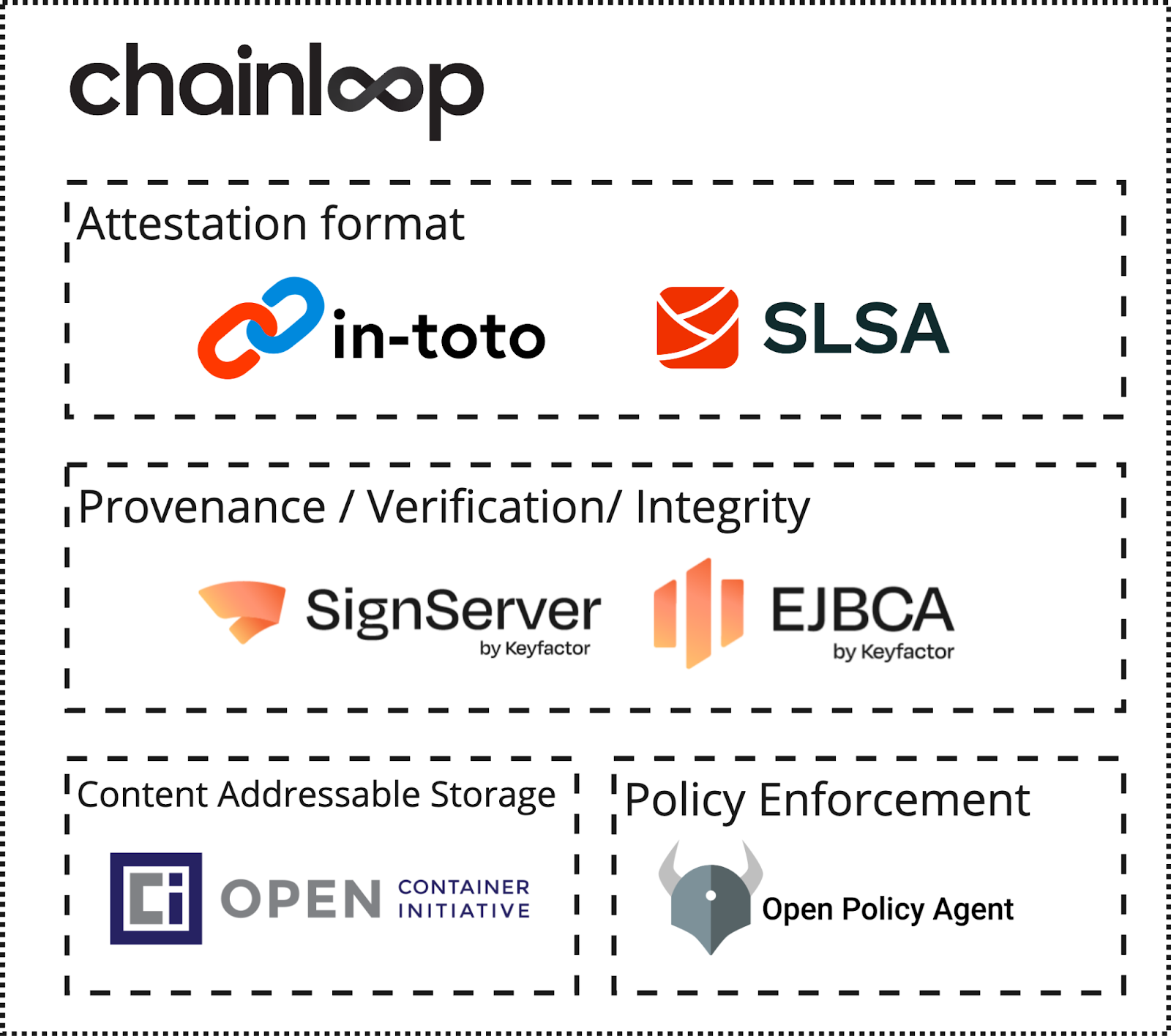
Chainloop and Keyfactor have partnered by integrating Chainloop’s modular evidence-based metadata storing platform with Keyfactor’s enterprise PKI solutions, EJBCA and SignServer. These integrations will allow organizations to collect, verify, trust, and protect the metadata generated by your Software Supply Chain.
We are announcing two new features: Remote signing with Keyfactor’s SignServer, and Local signing with Keyfactor’s EJBCA using ephemeral certificates.
You can read a detailed go-through of the integration in this link.
New material type: GitLab security reports
We recently added support for a new piece of evidence type: GITLAB_SECURITY_REPORT. SAST, Secret Scans, Dependency Vulnerabilities, Container Image Scans… all nine of them---are supported.
To start using only requires specifying the material type on the Chainloop contract:
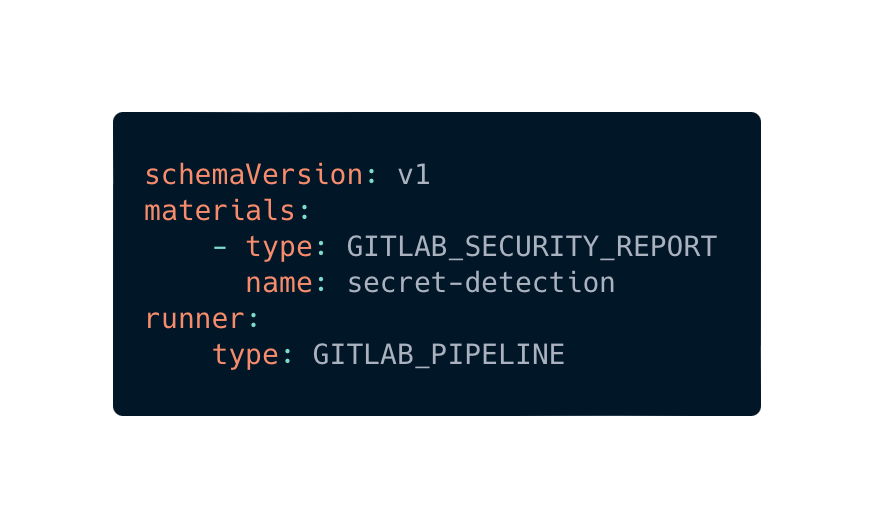
You can read more about the different types of reports on GitLab’s documentation.
The dagger module improvements
We have extended our Dagger module to be used beyond the attestation process. Now, users can also use it to create Chainloop workflows programmatically from CI/CD pipelines.
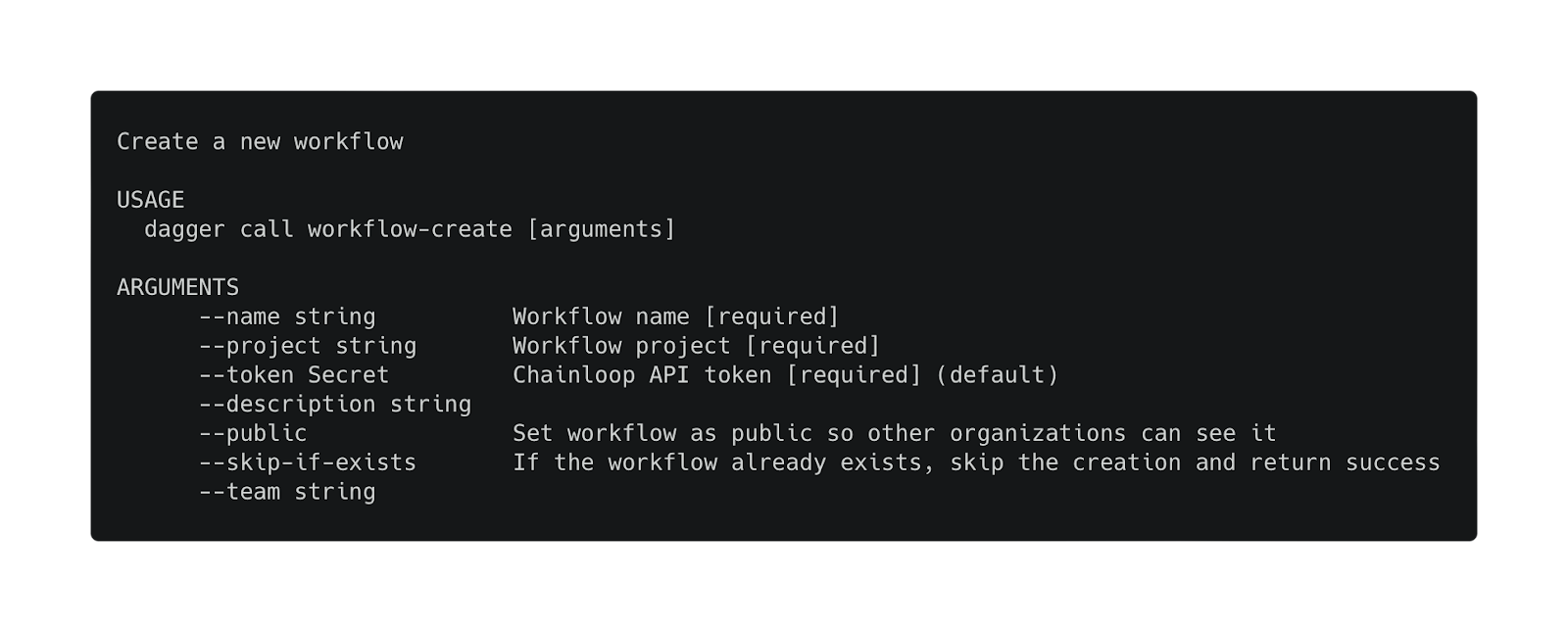
You can read about the module in the documentation published in Daggerverse.
Cosign and Notary signature information for Container image attestations
During the attestation process of a Container image, Chainloop can now automatically retrieve signature information from the target OCI registry. We currently support two types of generated signatures, Cosign and Notary.
All the information is stored as different annotations at the attestation. See the following example:
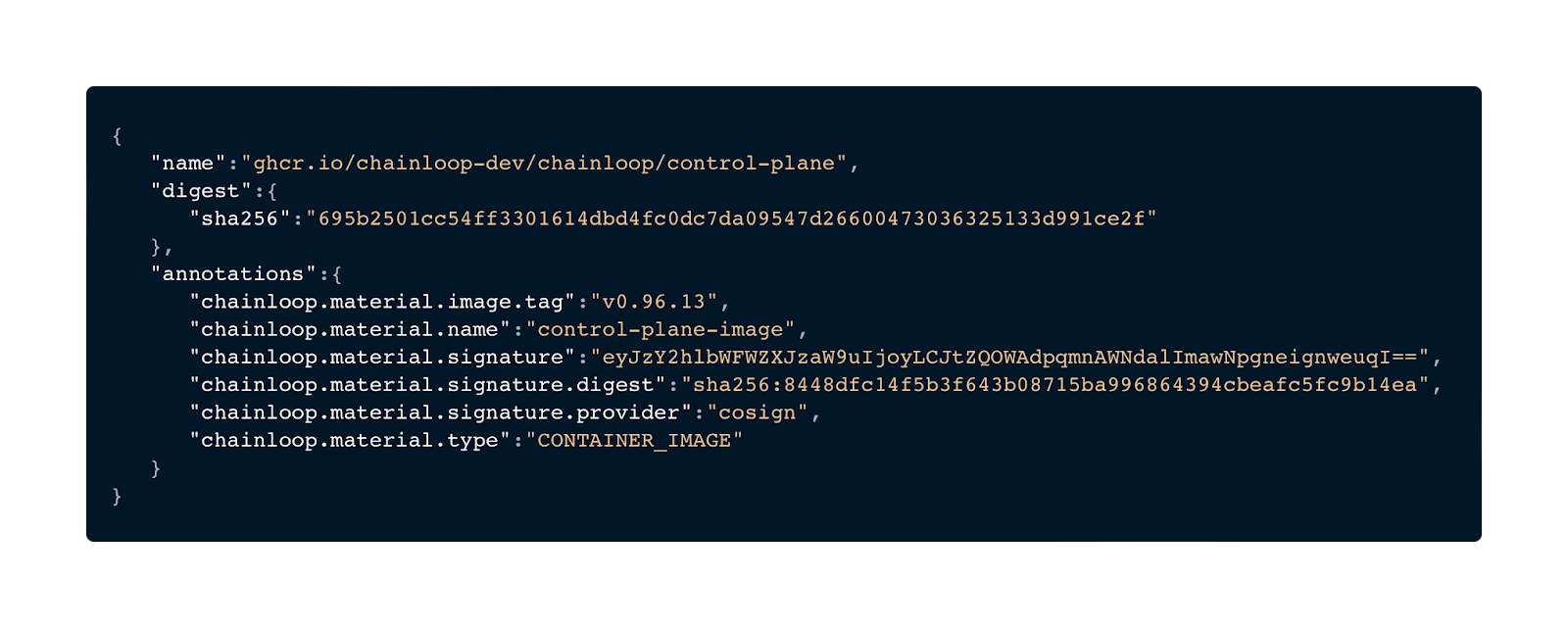
In there, you will see a few new annotations:
- chainloop.material.signature: The actual signature of the container image.
- chainloop.material.signature.digest: Digest of the OCI artifact pointing to the container image signature.
- chainloop.material.signature.provider: Tool used for the signing process.
This addition settles the grounds for policy enforcement.
Policies multi-kind
We have extended the capabilities of Policies with the concept of multi-kind policies. A multi-kind policy is a policy that can accept multiple evidence types (kinds) in the same specification. This is especially useful when a material can be specified in multiple format types (i.e SBOM as CycloneDX, SPDX, …), but from the user perspective, they still want to maintain one single policy. Let’s see an example:
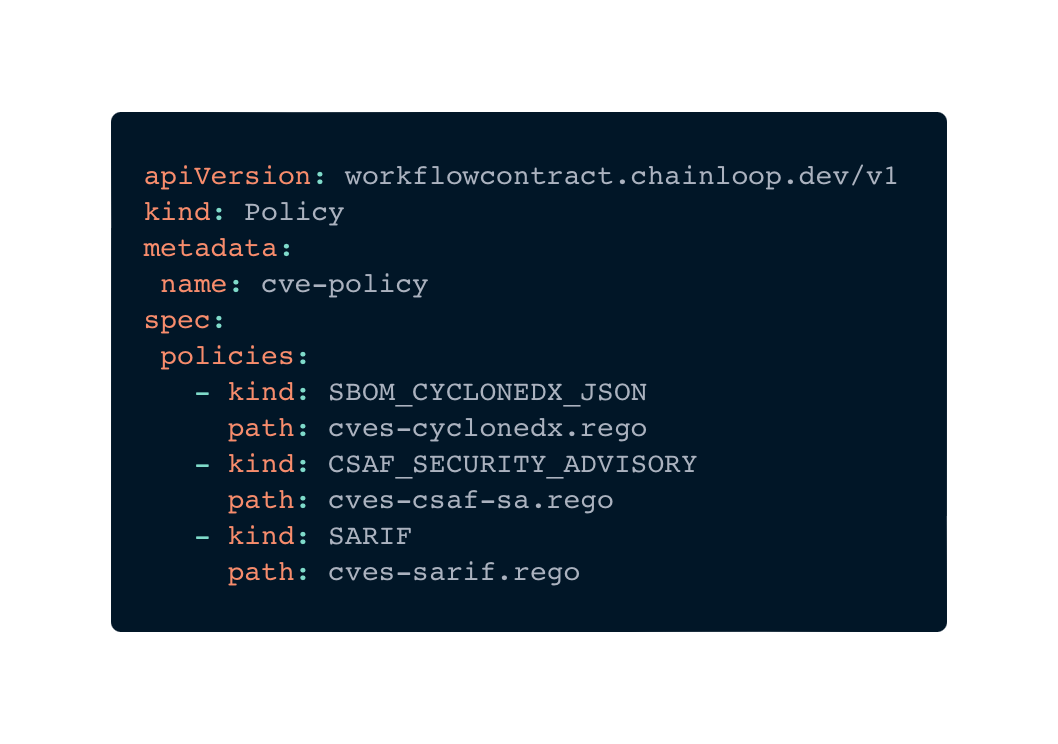
In the example above, the user could evaluate the same policy against a CycloneDX, CSAF Security Advisory report, or SARIF file. Chainloop will figure out which path script to execute. In this policy, the specific CVE detection method is determined by the type of evidence provided. This allows the policy to manage CVE checks based on the evidence type, all within a single, unified policy.
It is worth noting that the violations found on a multi-kind policy are the sum of all violations in all the different paths.
Policies dogfooding
In July, we announced the initial support for Policies in Chainloop. In August, we extended the support by allowing rules, arguments, and initial steps for policy providers. This month, we took all that groundwork and introduced policies in all CI/CD pipelines around Chainloop. You can see how we are using them declaratively in our repository.
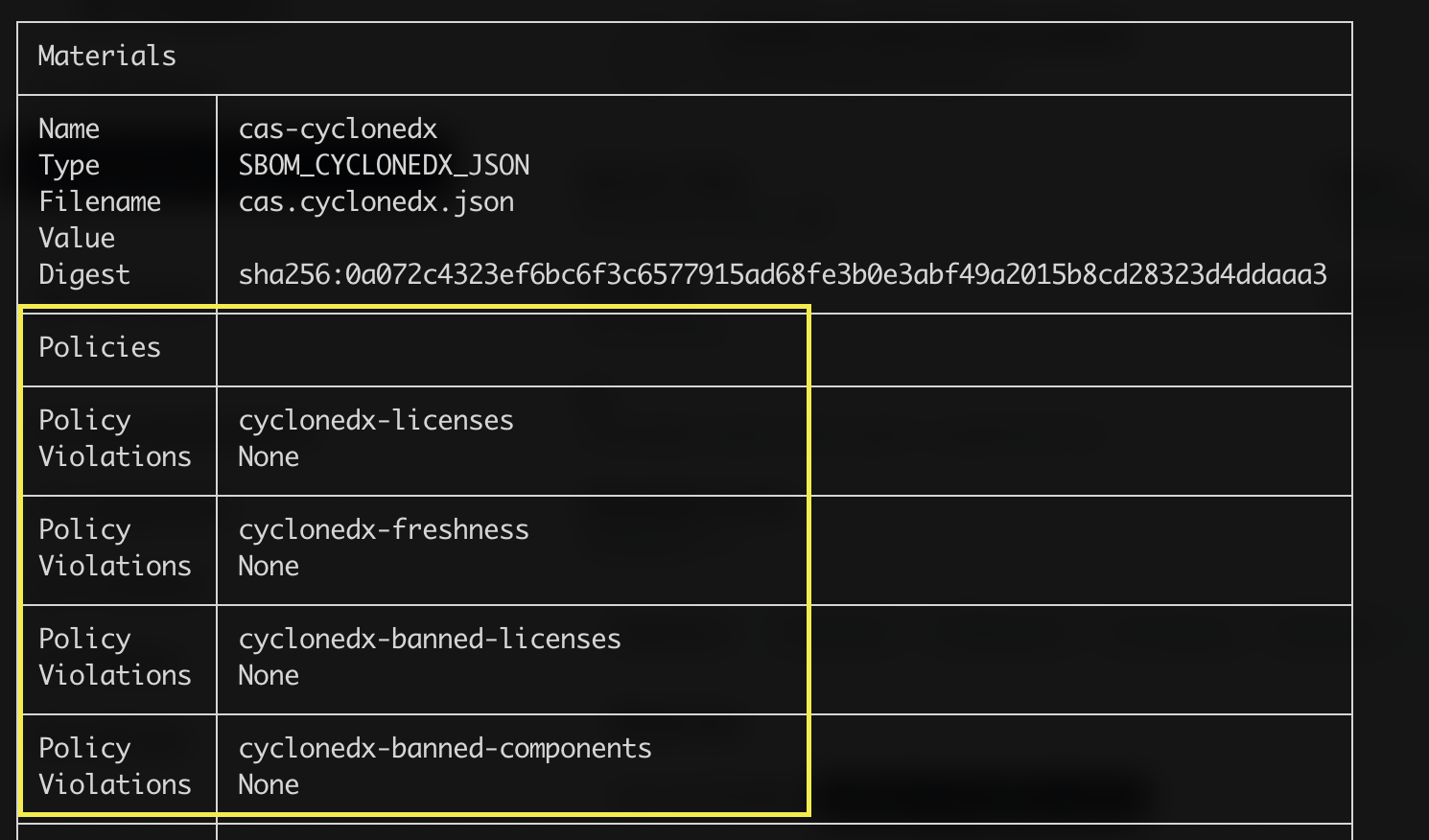
We believe policies are a game changer in the Software Supply Chain landscape. Be sure that in the upcoming months, you will hear more goodies being added to Chainloop.
Chainloop Platform
Now, let’s move into the features added to the Chainloop Platform, which builds on the open-source Chainloop Evidence Store. Currently, the platform is available for private early access both as a SaaS offering and for on-prem deployment.
New policies
We have introduced some new policies to the built-in library:
- Secrets detection: This policy scans secrets detection reports for any exposed or leaked credentials across your repositories. It supports multiple report formats, including GitLab’s secret detection reports and Gitleaks output, providing a comprehensive way to ensure no sensitive information is inadvertently exposed in your codebase or CI/CD pipeline.
- SARIF Vulnerability Detection for Trivy, Grype, and Twistlock: This policy analyzes vulnerability scanning reports in SARIF format, enabling detection of vulnerabilities by severity level or CVSS score. It supports a range of popular scanning tools, including Trivy, Grype, and Prisma Cloud (Twistlock), making it easy to enforce vulnerability thresholds in your CI/CD pipeline. This ensures that any vulnerabilities, particularly CVE entries below a defined risk threshold, are flagged before they become security risks in production.
- CSAF CWE Top 25 Detection: This policy checks SARIF reports for occurrences of Common Weakness Enumerations (CWEs), specifically those listed in the 2023 CWE Top 25 Most Dangerous Software Weaknesses. By integrating tools like SpotBugs and KICS, it identifies high-risk vulnerabilities related to software weaknesses commonly targeted by attackers, allowing you to prioritize remediation efforts on the most critical weaknesses in your code.
Software Bill of Materials (SBOM) Quality Gates
The generation of SBOMs is just part of the picture. One of the biggest challenges we’ve heard from our users and design partners is the need to standardize SBOM quality.
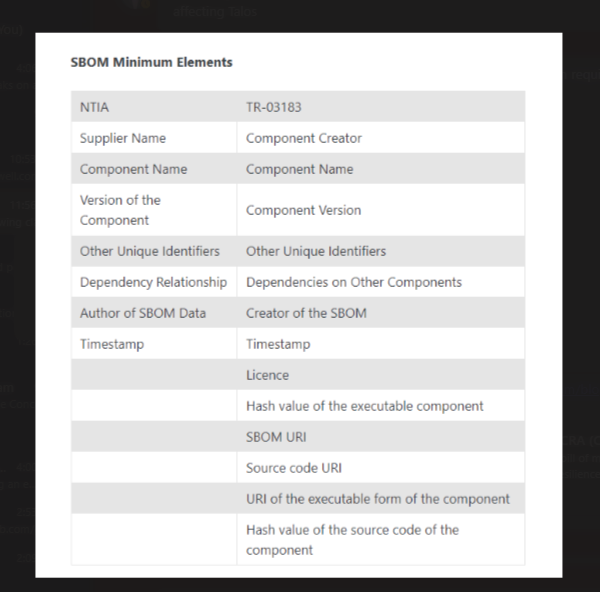
Quality is an overloaded term, but to us, it can be boiled down to
- Contains all the components; NTIA / TR-03183
- It was generated within a reasonable time window
- We know the tool that generated it and its version
- We can enforce the specification format and even version, i.e, CycloneDX 1.5
- It’s signed
- It has normalized license names, …
Those are excellent policy candidates, and as of today, most are already available in our built-in library of policies. We have a new feature in the works that will allow you to create groups of policies, so you should expect sbom-quality group, very soon :)
Windows support
Because not everything runs on Linux, we have extended the support for our CLI to Windows, so you can now use Chainloop CLI on Windows-based systems.
Special thanks
We want to take a moment to thank all our design partners for helping shape the product by addressing their unique use cases. The insights we’ve gained are truly invaluable. Here’s to more productive and meaningful collaborations ahead!
Chainloop HQ
Because coding has been just part of the job, let’s introduce some company/marketing-related news.
SOC 2 Type II Compliance

After working hard in the background for months, we proudly announce that Chainloop is a SOC 2 Type II Compliant. We chose to undergo a SOC 2 examination to ensure that our systems and processes meet industry standards for security and reliability. This examination helps us demonstrate our commitment to protecting your data and ensuring the consistent availability of our services. Please read more about the announcement in the following link.
Keyfactor Partnership

Chainloop has partnered with Keyfactor to deliver enterprise-grade security solutions that simplify and automate critical processes in the software supply chain. You can read more about the announcement here.
We were also invited to give a talk and a workshop during Keyfactor’s Community Day, where we demoed our SignServer and EJBCA integrations.

Open Source Summit and OpenSSF SOSS Community Day EU, Nordic Software Security Summit, Keyfactor’s Community Tech Meetup

The team has been on the move around Europe. We have attended several conferences and community meetups to hear first hand the problems customers face when enabling software supply chain security best practices on their processes.
We are happy with the results. We returned with batteries recharged, and soon, you will be able to see the outcomes of those conversations. Taking this moment to say thank you to all the people who show interest in Chainloop 😀
You can read more about what we have done on the events, here.
Wrapping Up
That’s all for September! We’re excited about these updates and hope they make your experience with Chainloop even better. Book a demo with us to see the new features in action. If you like what we’re doing, consider joining our community on Slack and giving Chainloop Open Source a star on GitHub.


