The Challenge
Supply chain attacks are increasingly common, and AI-generated code may often drastically increase the attack surfaces. In theory, release management works as a checkpoint to ensure that only verified, compliant artifacts are promoted to production. In reality, time and business pressures often take precedence.
Security scans can be time-consuming, and even false positives require thorough investigation, slowing down the release process. Vulnerability analysis and testing tools may not be perfectly integrated with DevOps pipelines, requiring separate data aggregation and analysis. Policies may be ambiguous or enforced incorrectly, allowing unverified artifacts to enter build pipelines.
The Chainloop Solution
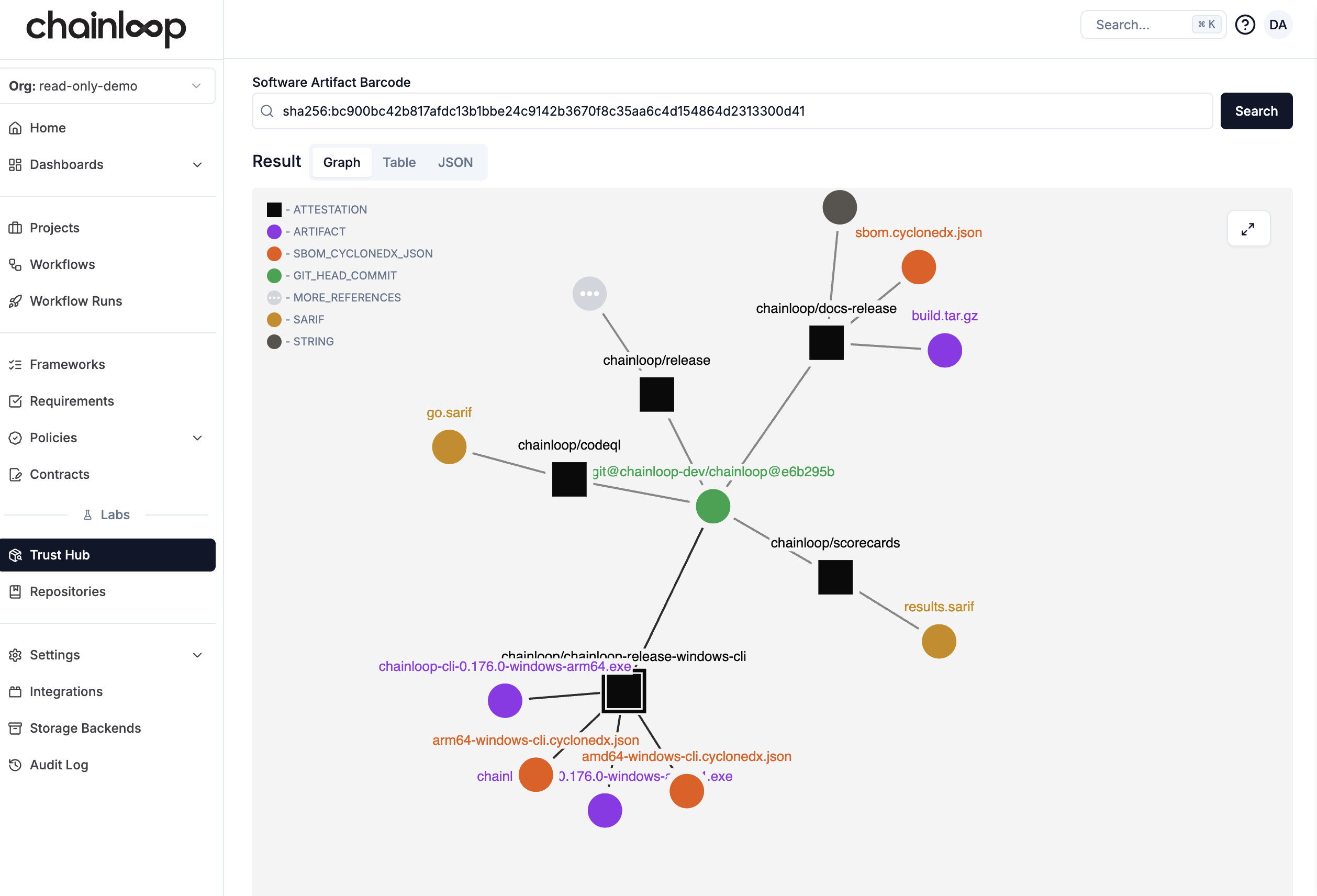
Chainloop takes a “security-first” approach to release management, enforcing end-to-end artifact provenance, signing, and integrity. It automatically captures and connects key evidence for every release artifact, including SBOMs, security scan results, code coverage checks, and other metadata.
It uses this metadata to automatically validate artifacts against pre-defined security policies, preventing the use of unverified or dangerous components. Acceptances, rejections, and exceptions are logged for every artifact and step in the release pipeline.